https://www.asustor.com/knowledge/detail/?group_id=1006
Q: How to set up router port for Let's Encrypt if you use ASUS router or some of the router that use 80 port by default?
2021-03-11
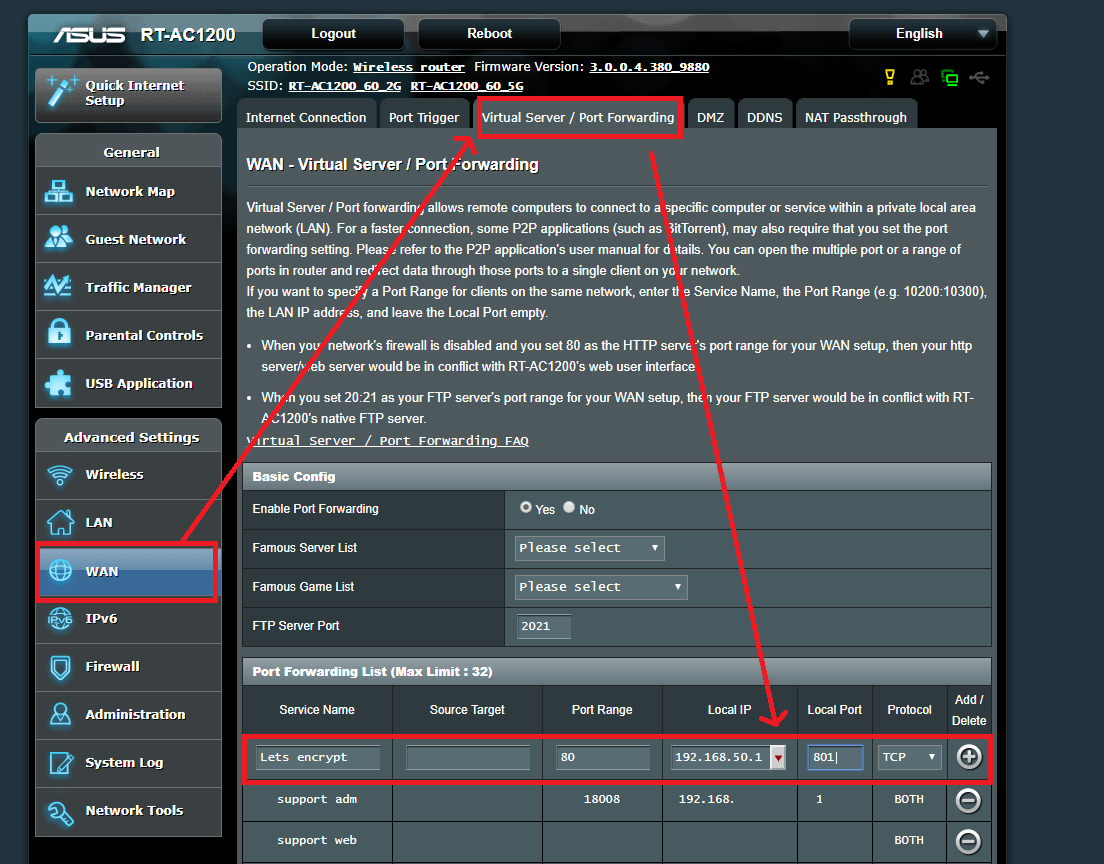
If you use ASUS router or some of the router that use 80 port by default, you have to manually go to router settings to set up 80 port with your NAS internal network IP to enable Let's Encrypt.
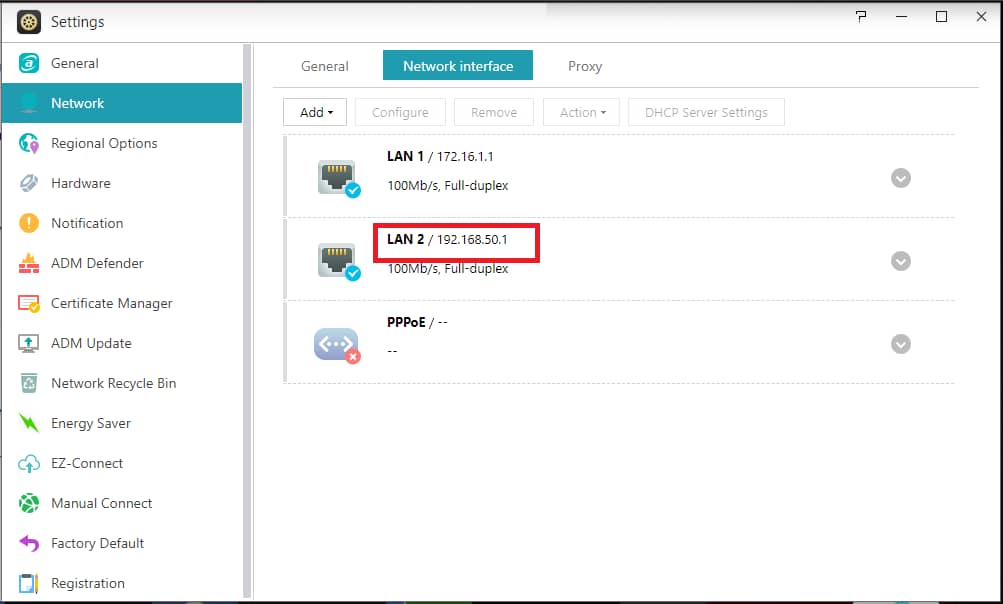
Your NAS internal network IP is 192.XX.XXX which can be found in Network settings like below picture.
ASUS Router settings:
You can change the local port to any non-80 port.
Sometimes, some router doesn't support 80 port even you setting up 80 port for port forwarding in router.
Please help to check the WAN IP + 80 port is working.
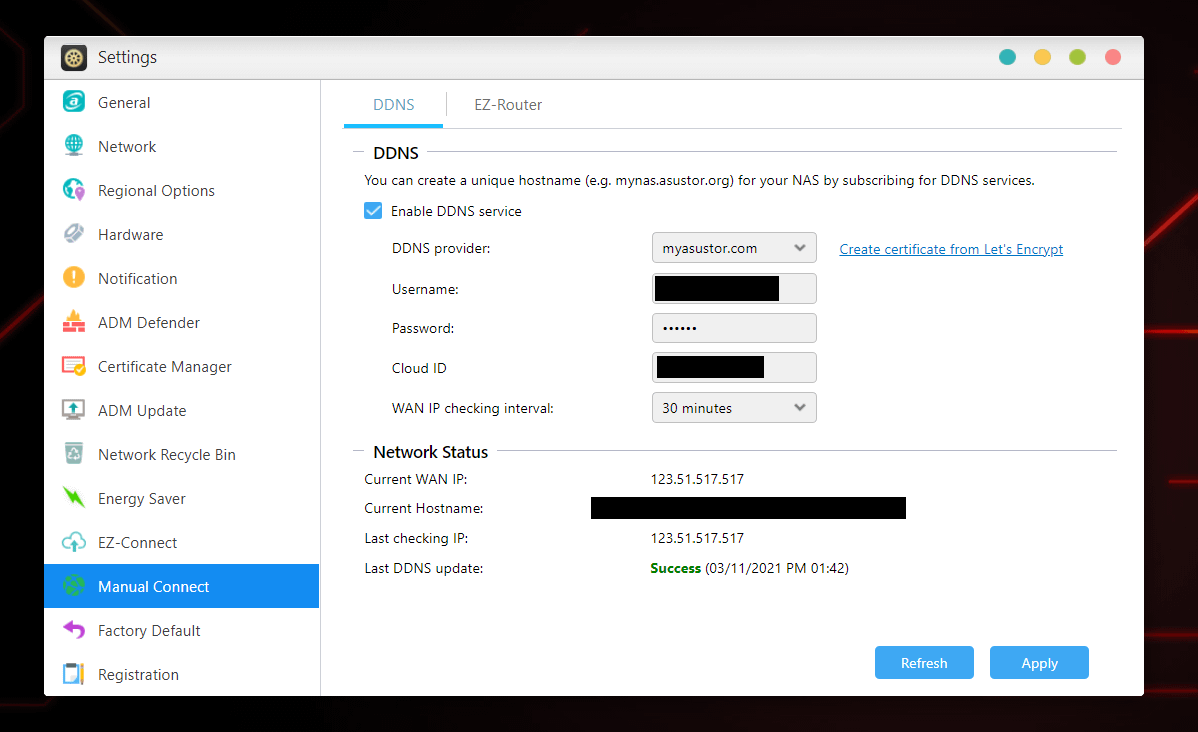
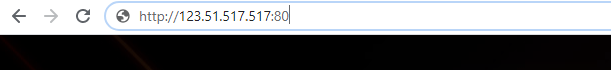
1.You can go to Manual Connect to find you WAN IP
\2. Type WAN IP and :80 in your browser address bar.
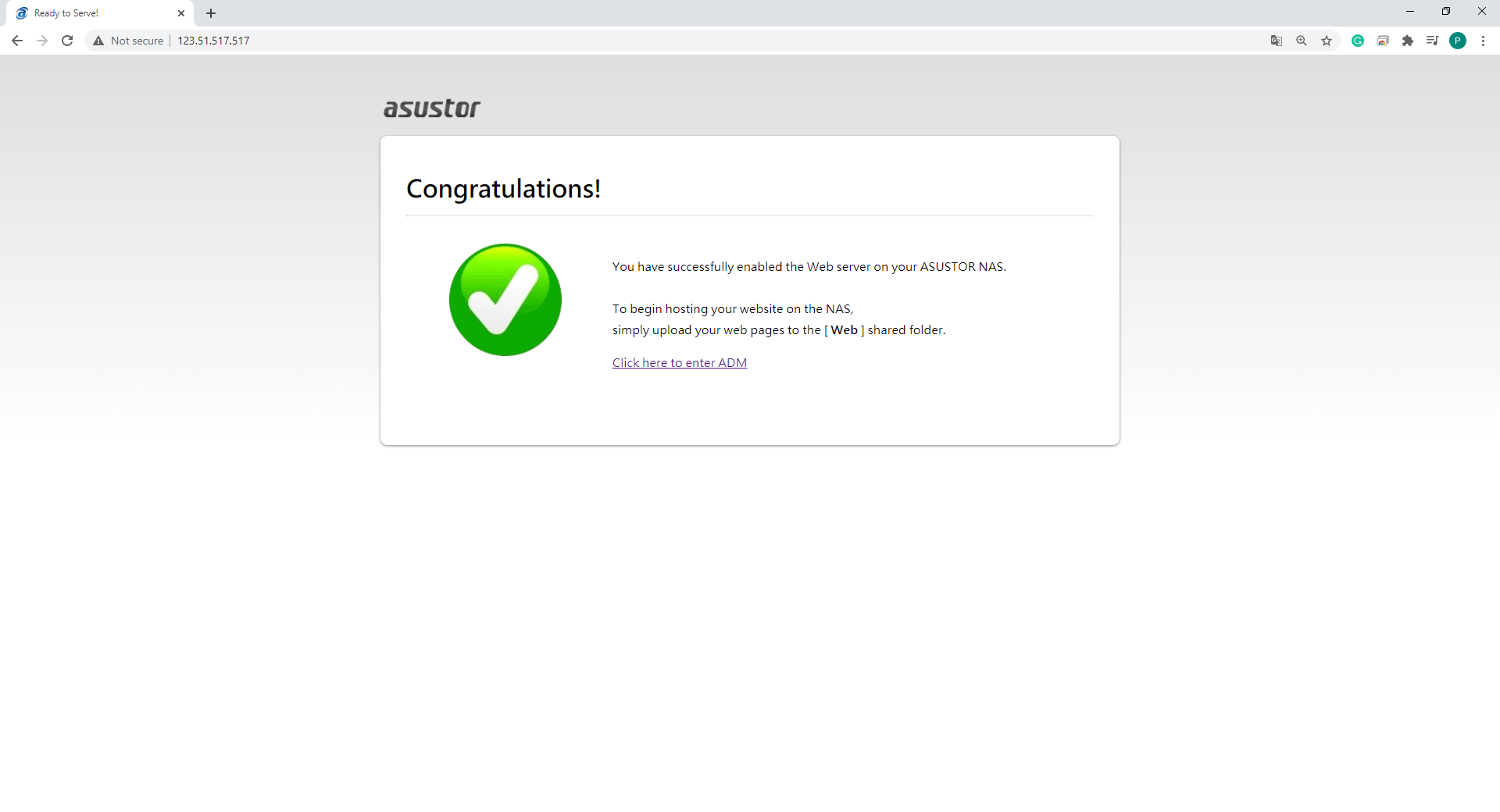
\3. If you can see the Congratulations page, then you can proceed to set up Let's Encrypt.
*If you are not able to see the Congratulations page by accessing http://NAS WAN IP from outside of the network, it means Let's Encrypt can't connect to NAS's Web Server to issue certificate neither.
Here is the procedure to troubleshooting this issue:
\1. Check if you can see the Congratulations page by accessing http://NAS local IP from the same local network as NAS unit.
\2. Change uplink router device to EZ Router compatible model and use ADM-Settings-Manual Connect-EZ Router to configure port forward:
https://www.asustor.com/en-gb/service/router?id=router
\3. Contact ISP support to check if port80 was blocked from ISP side.
If above steps not resolving the problem, please contact our support center for further help:
Generating CSR on Apache + OpenSSL/ModSSL/Nginx + Heroku
In order to activate your Certificate, you need a CSR code.
A CSR, or Certificate Signing Request, is a block of encoded text that you submit to a Certificate Authority when applying for an SSL Certificate.
It is typically generated on the server where the Certificate will be installed and should contain information about your website and business which will then be encoded into the Certificate.
- CSR Information
- Key Algorithm
- RSA Key generation
- ECC Key generation
- After the CSR is generated
- Possible Errors
CSR Information
Please ensure you fill out the CSR code details correctly. This should speed up the process of obtaining the SSL. Furthermore, the validation process for OV and EV SSL certificates requires that business details be entered accurately.
- Common Name (the domain name the Certificate will be issued for)
For example – example.comNote! For Wildcard certificates, the Common Name should be represented with an asterisk in front (e.g. *.example.com).
- Country (two-letter code)
Country (C) – the two-letter code of the country where the company or applicant is located (for example, GB for Great Britain or US for the United States; you can check your country code here.)
- State (or province)
State (S) – the state, county or region the company or applicant is located in (e.g. California).
- Locality (or city)
Locality (L) – the city where the company or applicant is located (e.g. Los Angeles). This parameter should not be abbreviated.
- Organization (your company name. Feel free to put “NA” here for any Domain Validated certificate)
Organization (O) – the officially registered name of the organization that is applying for a certificate (e.g. Namecheap Inc.). For Organization and Extended Validation certificates, Certificate Authorities will be verifying the submitted organization. For Domain Validation SSLs, this field is not critical and the details will not be listed on the issued certificate; however, it should at least be filled in with “NA”.
- Organizational Unit (department. Feel free to put “NA” here for any any Domain Validated certificate)
Organization Unit (OU) – the name of the department or division within the submitted organization (e.g. SSL Support).
- Email address (put a valid email address here)
Email Address – an email address of the company or the applicant. This field is optional.
Note! This email address won’t be used during the verification process, unless a mistake is found with any of the submitted details. However, this email will be considered an admin contact, unless you change it during the activation process. The SSL will be issued to the admin contact email address once it is activated.
- Challenge Password and Optional Company Name – please do not use challenge password and leave Optional Company Name field empty too. These values are now obsolete and may cause issues with getting the SSL certificate.
Key Algorithm
Generally, OpenSSL is used for CSR generation on Linux-based web servers (Apache or Nginx) So, if the default web server is installed, there should be no issues with using OpenSSL as it is installed by default on these web servers.
Now, you need to decide which key algorithm you want to use.
RSA key algorithm is the most commonly used algorithm nowadays. Click here for details.
ECDSA key algorithm is a modern technology that is used for the creation of ECC certificates. Details are here.
| SSH SetupThe CSR will be generated on the server side, so you will need to connect to it via the SSH.
SSH, also known as Secure Shell or Secure Socket Shell, is a Network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network. In order to connect to your server via SSH, you will need the IP-address, username, password and SSH client (any will do, for example: ZOC Terminal; PuTTY; OpenSSH; MobaXterm; SecureCRT) installed. The IP-address, username, and password can be obtained from your hosting provider. |
|
File location We recommend creating a folder to safely store the SSL files in. This folder can also be used to run the commands to generate the CSR. When you generate a CSR (.csr file), a Private key (.key file) will be generated at the same time. It is critical that you don’t lose the Private key as it will not be possible to get another one later. A Private key that corresponds to an SSL is necessary for installation. If you lose the Private key, you will need to generate another CSR and restart the whole process. Please do not share your Private key with anyone. This is bad practice; it must remain private at all times. One of the key reasons is that the Certificate Authority can revoke a certificate if its private key was compromised. You can create an SSL folder in your home directory as an alternative option. Please use the following command to do so:
Then, move to that folder by running:
|
RSA
The RSA algorithm is an asymmetric cryptography algorithm. This basically means that there are two keys involved while communicating, i.e., the Public key and Private key. The RSA key algorithm is the algorithm most widely used in digital security. You can refer to this article for more information.
You can run the following commands to generate the CSR. We recommend running this command in the folder where you will store the SSL files to avoid confusion later on.
openssl req -new -newkey rsa:2048 -nodes -keyout server.key -out server.csr
Note! To avoid confusion, we recommend replacing server.key and server.csr with the real domain name the certificate will be issued for. Those will be underlined in the commands.
For example:
openssl req -new -newkey rsa:2048 -nodes -keyout yourdomain_tld.key -out yourdomain_tld.csr "
When you run the command, you will be prompted to enter the values (Common name (CN), Locality (L), State (S), Country (C), Organization (O), Organization Unit (OU), Email Address) in the terminal. You can refer to this section to find out which information should be entered.
Warning! If the command fails, please refer to this section here.
The CSR should not contain characters such as ‘?’, ‘@’, ‘#’, ‘$’, ‘%’, ‘^’, ‘&’ and ‘*’ as they will cause issues. The only non-alphanumeric character permitted is the backslash ‘\’.

It is possible to generate a CSR with the following command:
openssl req -nodes -newkey rsa:2048 -keyout server.key -out
server.csr -subj "/C=GB/ST=Yorks/L=York/O=My Company
Ltd./OU=IT/CN=example.com"
You will need to specify the details in the command itself. You can refer to this section for the details that should be included.
| Additional Flags in the CSR RSATo generate a CSR code with the Street address value included, add the ‘Subject’ (‘-subj’) tool with the corresponding data to the command as follows:
The command with the zip code included in the address should look like this:
It is also possible to generate a CSR for a Multi-Domain SSL certificate via one line with all SANs (Subject Alternative Names).
|
ECC
The Elliptic Curve Discrete Logarithm Problem (ECDLP) needs to be solved in order to break the ECDSA key, and there has been no major progress so far to achieve this. Thus, an ECC certificate provides a better security solution and is more difficult to break using the usual hacker’s “brute force” methods.
You can run the following commands to generate a CSR. We recommend running this command in the folder where you will store the SSL files to avoid confusion in the future.
In the OpenSSL cryptographic library you can use this algorithm for CSR code generation by using the commands below:
openssl ecparam -genkey -name secp384r1 | openssl ec -out ecc.key
openssl req -new -key ecc.key -out ecc.csr
Note! You will need to run the first command before running the second one as the CSR will be based on the key that’s generated by the first command. So, you need to make sure the name of the file matches.
Warning! If the command fails, please refer to the section here.
Example:
You run:
openssl ecparam -genkey -name secp384r1 | openssl ec -out yourdomain.key
Then, the next command will be:
openssl req -new -key yourdomain.key -out ec.csr
Note! When you run the second command, you will be prompted to enter the values (Common name (CN), Locality (L), State (S), Country (C), Organization (O), Organization Unit (OU), Email Address) right away in the terminal. For more information, refer to this section about which information should be entered.
Note! The CSR should not contain characters such as ‘?’, ‘@’, ‘#’, ‘$’, ‘%’, ‘^’, ‘&’ and ‘*’ as they will cause issues. The only non-alphanumeric character that can be used is the backslash ‘\’.

| Additional Flags in the CSR ECCIt is also possible to generate a CSR for a Multi-Domain SSL certificate via one line with all SANs (Subject Alternative Names).
The command can be modified with the -addext san extension as well as -subj to make a proper one liner:
|
After the CSR is generated
Once you’ve generated your CSR you can use it to activate your SSL certificate.
To do this, you will need to copy the CSR code. Do this by running the command:
ls
You should see a list of the files present in the current folder.
Locate the file with the “.csr” extension and open it with this command:
cat filename.csr
Here, “filename” should be substituted with the name you specified in the CSR generation command.
The CSR code will begin and end with the following tags which should be copied too:
—–BEGIN CERTIFICATE REQUEST—–
—–END CERTIFICATE REQUEST—–
Possible Errors
When you run the previously mentioned commands, you may encounter the following error message: “OpenSSL is not recognized as an internal or external command”
This could mean that the OpenSSL library was not installed or the %PATH% specified during the installation process was not correct.
You can verify the installation of the OpenSSL library via this command:
dpkg -l 'openssl*'
You should get a response featuring “ii”. If the response does not contain “ii”, it means that there are issues with OpenSSL Libraries. If this is the case, you will need to contact your hosting provider/web-developer.

https://www.namecheap.com/support/knowledgebase/category/14/ssl-certificates/
SSL General
Basic information on SSL certificates
SHA-2 server and browser compatibility
What is an ECC (Elliptic Curve Cryptography) certificate?
How do I get an ECC certificate via Namecheap?
Why an EV certificate is better for an ecommerce website than a Domain Validation one?
What is the difference between very high, high, medium and low assurance certificates?
Activation
How do I activate an SSL certificate
How do I activate a Multi-Domain SSL certificate?
Supported key sizes and signature algorithms in CSRs
How to enable an SSL certificate
SSL certificate activation and installation for domain(s) hosted on Namecheap hosting servers
Validation
Contact Comodo (now Sectigo) Support
No, I have not received the DCV (approval) email
I completed DCV but the order is not issued (Brand validation)
How to complete HTTP-based validation ('Upload a validation file' option)
Installation
How to install SSL certificates
How can I find the private key for my SSL certificate
Can I download an issued certificate on your site?
Where do I find SSL CA Bundle?
Reissuance
Why would I need to reissue my certificate?
How do I reissue my SSL certificate?
I changed my server IP address, do I need to reissue the certificate?
What should I do if my Private Key was lost or deleted?
Renewal
When can an SSL certificate be renewed?
How to renew an SSL certificate
Can I use my old CSR for SSL renewal?
Can I avoid activation process upon SSL renewal?
If I renew SSL certificate 30 days before it expires, will I lose the time remaining on it?
cPanel SSL Plugin
1-year free cPanel PositiveSSL certificate offer
What is ‘Namecheap SSL’ and how do I use it?
What products does your SSL cPanel plugin support?
How do I reissue an SSL certificate with your cPanel plugin?
Can I use an already issued SSL with your cPanel plugin?
Multi-Domain SSL Certificates
What is a Multi-Domain SSL certificate?
How many domains can I secure with your Multi-Domain SSL certificate?
Can I add another domain later, after the SSL certificate has been issued and activated?
How can I change the number of additional domains or change the domain itself?
What about CSR code SAN fields?
Cancellation
How can I revoke my certificate?
How to cancel an SSL certificate? Will there be a refund?
Will you cancel my certificate if I do not respond to the approval email?
Browser errors
I get "Certificate is not trusted because it is self-signed" error message when I visit my site
Why do I get "Common name mismatch" error in my browser?
SSL notifications in Chrome and their meaning
My SSL is installed, why do I get the warning ‘Not secure’ in browsers?
Firefox error code: ssl_error_rx_record_too_long
Site Seal, Logo
I want my Site Seal to appear as a pop-up on my site
SSL installation errors
Troubleshooters on how to resolve certain errors one may face during certificate installation
Firefox error code: ssl_error_rx_record_too_long
Apache error: X509_check_private_key:key values mismatch
CA Bundle is not updated after reinstalling certificate through cPanel
SSL Certificates
Here you can find information on what SSL certificates are used for, SSL certificates that Namecheap offers and SSL related procedures such as activation, installation and other
Generating a CSR on Mac OS X Server/Yosemite/El Capitan
Generating a CSR on Sun Java System Web Server 7.x
Generating CSR in Exchange 2013 EAC
Generating CSR in Exchange 2013 Shell
Generating a CSR code on IIS 8&10
CSR generation on a GlassFish application server
CSR generation on Google Cloud services
How to generate a CSR code on a Windows-based server without IIS Manager
CSR generation on Exchange 2010
Generating a CSR on Plesk Onyx
Generating a CSR on Citrix NetScaler VPX
Generating a CSR code on Windows using Certeq
Generating a CSR on Mac OS using Keychain
Sectigo Root Certificate expiring May 30, 2020
Generating a CSR on Tomcat using a keytool
Generating a CSR code using DirectAdmin
Generating a CSR in Exchange 2007 (PowerShell)
Generating CSR on Apache + OpenSSL/ModSSL/Nginx + Heroku
Generating a CSR on Amazon Web Services (AWS)
Domain & CSR code setup for Synology NAS
How to Generate CSR (Certificate Signing Request) Code
How can I complete the domain control validation (DCV) for my SSL certificate?
How do I reissue my SSL certificate?
Can I download an issued certificate on your site?
SSL notifications in Chrome and their meaning
How to install SSL certificates
https://www.namecheap.com/support/knowledgebase/subcategory/38/ssl-general/
SSL General
Basic information on SSL certificates
SHA-2 server and browser compatibility
What is an ECC (Elliptic Curve Cryptography) certificate?
How do I get an ECC certificate via Namecheap?
Why an EV certificate is better for an ecommerce website than a Domain Validation one?
What is the difference between very high, high, medium and low assurance certificates?
Your site shows 256-bit encryption and my site shows 128-bit, why?
How 2–5-year SSL certificates work
What is Certificate Transparency?
HTTP to HTTPS redirection on IIS
HTTP Strict Transport Security (HSTS)
HTTP Public Key Pinning (HPKP)
Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows
I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?
Perfect Forward Secrecy. What it is?
How to check whether the server supports Forward Secrecy?
How to push SSL certificates from one Namecheap account to another one
Prerequisites for Namecheap Shared hosting to enable HSTS
>
How to check if HSTS is enabled
What is SSL certificate encryption strength?
How do I get A+ rating in SSLLabs?
How to use .htaccess to redirect to https in cPanel
Advantages of having an SSL certificate
Setting HTTPS redirect on a Nginx web-server
Supported key sizes and signature algorithms in CSRs
How to check the certificate revocation status
CAA Record and why it is needed (SSL related)
Cipher Suites Configuration for Apache, Nginx
SSL Certificate Validity Update
I need to secure some of the subdomains of my domain name
I need to secure two, three or more domain names with the same certificate
What is an SSL certificate and what is it used for?
What is Certificate Authority (CA)?
SSL certificate migration from the SHA-1 to SHA-2 algorithm
How do I check my hashing algorithm?
I want to test your service do you have trial certificates?
Can I use a single SSL certificate for multiple subdomains?
How to inform your clients that you use SSL
What is a wildcard certificate?
Types of certificates offered at Namecheap
Are your certificates private or shared? What is the difference?
Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?
Can I use your SSL certificates for FTP and SQL?